I'm Jiuma Elhshik
cybersecurity professional

About me
Introducing me, myself and I
personal information
I am a dedicated cybersecurity professional with a strong blend of technical expertise and interpersonal skills. With hands-on experience in cybersecurity consulting, risk assessment, and incident response, I excel in providing tailored solutions and enhancing security postures for diverse organizations. With past experience and familiarity in multiple programming languages and advanced security tools, I am passionate about optimizing IT infrastructures, performing security audits, and automating processes to improve operational efficiency. My leadership roles and participation in prestigious programs demonstrate my commitment to continuous learning and professional growth, making me a valuable asset to any cybersecurity team.
Name : JIUMA ELHSHIK
Email : [email protected]
Phone : (763)-438-8517
My skills
What I know and am learning
Software/Tools
-

VMware
-

Salesforce
-

Linux
-

Wireshark
-

Kaseya
-

SolarWinds
-

Grafana
-

Jira
-

Cisco Meraki/Umbrella
-

Microsoft Security Suite
-

Proofpoint
-

Abnormal
-

KnowBe4
-

Cortex XDR
-

Windows Server/Active Directory
-

SQL
-

Tableau
-

Apache
Programming/Scripting
-

Python
-

C
-

Bash
-

PowerShell
-

SQL
Soft Skills
-

Security auditing
-

Risk management
-

Proactive leadership
-

Interpersonal communication
-

Strategic planning
-

Organizational efficiency
-

Adaptable learning
-

Critical thinking
-

Attention to detail
Latest Projects
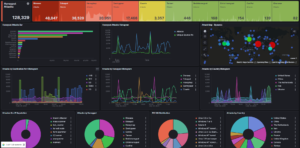
Trap the Hackers: Building and Troubleshooting a T-Pot Honeypot (Part 1)
Deployed a honeypot on AWS, and collected data from over 120,000 internet attacks. Read more about this project on my Medium blog!
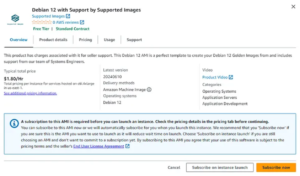
Configuring Secure Cloud Networks with VPN and NAT on AWS: A Personal Project
Constructing a Secure Cloud Network between multiple cloud regions with a fully functional VPN tunnel!
Ethical Hacking: Attack, Analyze, Fortify
Individual Video Project - I present to my class about the basics of Ethical Hacking, and perform a practical hacking demonstration for them!
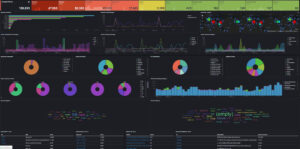
Trap the Hackers: Leveraging T-Pot for Threat Intelligence (Part 2)
Deployed a honeypot on AWS, and collected data from over 120,000 internet attacks. Read more about this project on my Medium blog!

